Ensure that your Azure resources consistently meet your organization’s standards and security requirements. Terraform Compliance is a resource-efficient tool that detects misconfigurations early.

By Olga Kalyayeva, Cloud Solution Architect
Compliance is an ever-evolving responsibility in cloud computing. As infrastructure continuously changes, there’s a need to align with both regulatory and internal company rules.
If mismanaged, compliance can become burdensome and costly. The objective is to identify as many misconfigurations as possible, ideally during development. Discovering issues later tends to be more expensive and more complex for developers to resolve.
Why Terraform Compliance is the Top Choice
Specializing in the Azure cloud, I’ve assessed numerous tools for efficient infrastructure compliance. I settled on Terraform Compliance, paired naturally with Terraform. Terraform Compliance is an open-source framework designed to test and enforce compliance policies in infrastructure code. It ensures your infrastructure configurations adhere to your organization’s or regulatory standards concerning security, compliance, and best practices.
Understanding Azure Policy Effects
Before diving into Terraform Compliance, let’s understand Azure infrastructure governance and compliance. To maintain compliance in Azure Cloud, you’ll work with Azure Policy and address any infractions. Azure Policy effects dictate actions when a policy rule aligns with a resource during an evaluation. Here are the primary effects:
- ‘Append’: Introduces specific fields or parameters during resource creation or updating.
- ‘Audit’: Logs a warning when a policy breach occurs during creation or updating but doesn’t halt the process.
- ‘AuditIfNotExists’: Logs a warning if a certain condition isn’t met.
- ‘Deny’: Blocks resource creation or updating if it breaks the policy.
- ‘DeployIfNotExists’: Initiates a remediation task to deploy a resource if a specific condition isn’t met.
- ‘Disabled’: Deactivates the policy rule. No evaluations occur, and the effect is nullified.
- ‘Modify’: Alters particular fields or parameters during resource creation or update. (Currently in preview).
‘Audit’ policies inform you of resource misconfigurations and non-compliance, while ‘DeployIfNotExists’ fixes configuration issues during deployment. ‘Deny’ policies obstruct the deployment of non-compliant resources.
Enhanced IaC Compliance with Terraform Compliance
While Terraform’s Infrastructure as Code (IaC) in Azure can administer compliance checks, it’s not flawless. For instance, with ‘Deny’ policies, a failed Terraform deployment might leave the root cause ambiguous. Policies like ‘DeployIfNotExists,’ ‘Append,’ or ‘Modify’ can convolute the Terraform state file, leading to inaccurate outcomes.
Terraform Compliance addresses these hurdles by enabling negative IaC tests. While it doesn’t wholly manage compliance, it significantly augments IaC compliance by pinpointing misconfigurations early, offering transparent feedback. Combined, these strategies culminate in a resilient, compliant Azure Cloud infrastructure.
Installing Terraform Compliance in a DevOps setting and integrating it into build pipelines is straightforward. You can find a lightweight test framework at Terraform Compliance.
How to Use Terraform Compliance: Sample Test Cases
To illustrate Terraform Compliance usage and automation, consider the following test cases.
1. Evaluating a single condition:
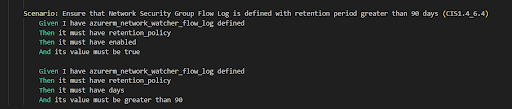
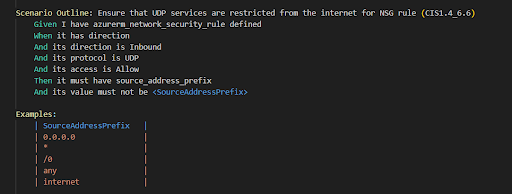
2. Running an array check, e.g., verifying NSG rules, so in this test case <SourceAddressPrefix> will be replaced with values from array and the test will be done 5 times – 1 for each value:
3. Terraform Compliance clarifies coding discrepancies:
You can see which resource is not compliant with which requirement. The screenshot shows 4 storage failed accounts because they didn’t have blob_properties. You also can figure out the names of failed blob_storages.
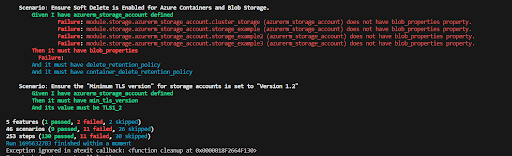
Note that nuances always exist when framing steps for accurate checks. Consequently, I suggest using test codes to confirm the validity of the test cases.
4. Making exclusions for specific test cases:
You can specify resource names to be ignored in the test cases.
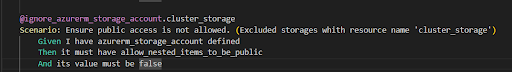
Note that nuances always exist when framing steps for accurate checks. Consequently, I suggest using test codes to confirm the validity of the test cases.
Optimal Compliance with Minimal Resources
Both Terraform Compliance and Azure Policy can synergize to guarantee your infrastructure mirrors your organization’s compliance requirements. While Terraform Compliance doesn’t answer all compliance challenges, it substantially optimizes IaC compliance. It detects early misconfigurations, provides lucid feedback, and allows test case customization—all with minimal resources. As a result, you achieve enhanced compliance efficiently and cost-effectively.
We’re here to assist you on your Azure journey
For more insights on Azure infrastructure compliance or knowledge sharing, you are welcome to reach out to Olga at olga.kalyayeva@devoteam.com. If you have any other inquiries, you can contact us via the button bellow.